How to Choose the Right Tools to Protect Your Digital Life

There are many cybersecurity and privacy products available to protect your digital life. All of which claim to be the best. But how do you know which one is right - for you?
It can be difficult to choose between different products and services, as they can seem similar and different at the same time. How do antivirus, identity protection services, VPNs, password managers work to keep you safe online, and what makes them different from each other?
Let’s take a closer look at how all these solutions can work together to protect your online activity.
New Cyber-Threats Need Special Countermeasures
Where do we draw the line between our online and offline activities? The Internet is all around us.
Whether we use it consciously, as part of our daily routine, or unwittingly, because it is built into the products and services we rely on, the Internet is always there. Technology is now heavily dependent on it to function properly and provide us all with the benefits of a modern, comfortable life.
The increased connectivity has also led to more opportunities for cyber-criminals to exploit technology and people. It is important to remember that:
"Crime, whether it happens in the physical world or in the digital space […] is deeply rooted into some minds. So what cyber criminals are attempting to do is use technology – what we call the cyberspace – to run criminal activities that they used to run in the physical world."
Bogdan Botezatu (Director of Threat Research and Reporting, Bitdefender)
And the threat landscape is virtually infinite. Therefore, the technologies used to mitigate them must be able to cover segments of each type of threat.
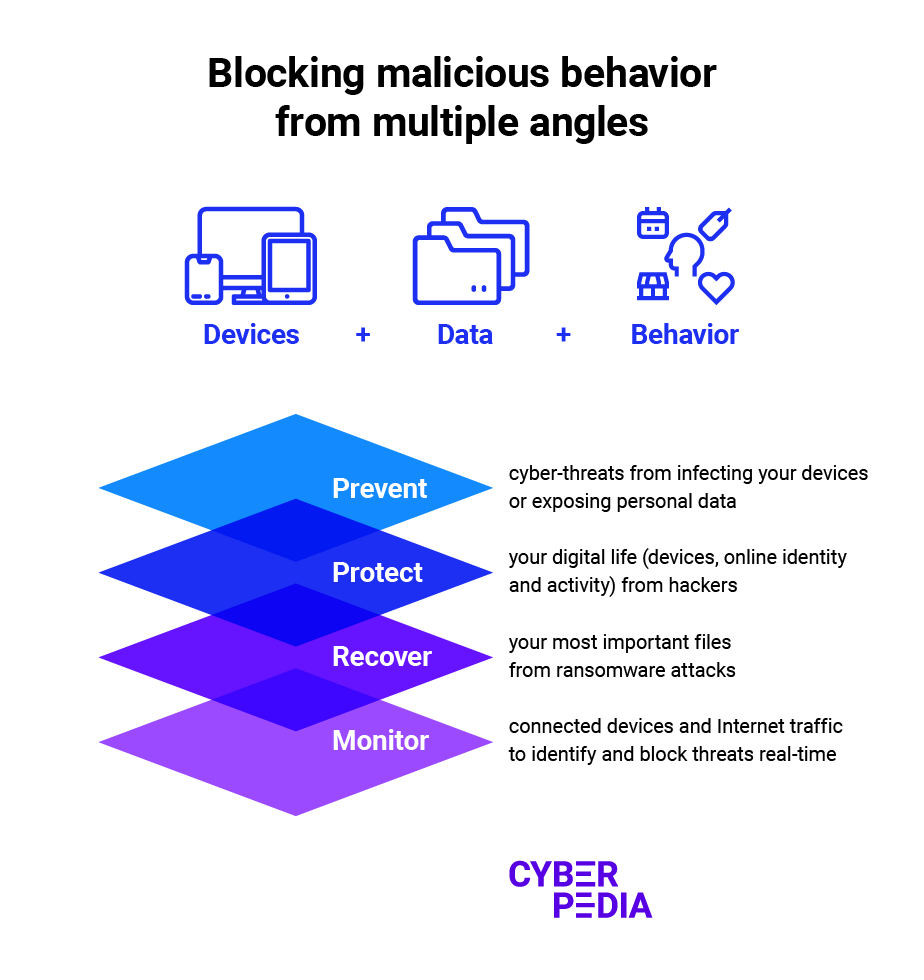
The main security layers against cyber-attacks focus on these four major goals:
- Prevent: Stop hackers from interfering with your data, files, accounts, and other digitized aspects of your life.
- Protect: Counteract cybercriminal tactics when they manage to reach your devices and data.
- Recover: Isolate and quarantine malicious software so it cannot spread further to compromise your devices and data.
- Monitor: Audit the data you store locally on your devices, the incoming Internet data, and your personal data shared online to detect risks from malicious activity.
Why Security and Privacy Solutions Adapt to Different Needs
Keeping all these essential security layers in mind, here is why different cybersecurity and privacy solutions are required for different needs:
Different Goals and Capabilities
From antivirus and VPN to digital identity protection and password manager, every solution focuses on a particular category of cyber-threats.
"Everything happens in layers because some are more proficient at detecting specific threats than others."
Bogdan Botezatu (Director of Threat Research and Reporting, Bitdefender)
Flexibility and Freedom of Choice
Balancing convenience, performance, proficiency, and user friendliness is a demanding challenge for cybersecurity specialists.
"By dividing a large product into modules that take care of individual functions, we allow people to mix and match offerings.
Having different modules that integrate with one another helps the user get the most out of a security suite.
For some people, this kind of flexibility is more important than having all the products integrated into one ecosystem."
Bogdan Botezatu (Director of Threat Research and Reporting, Bitdefender)
Whether you prefer to mix and match your own building blocks to protect your digital footprint, or you’d rather have a one-stop-shop for everything you need, there are plenty of options to select from. And that’s a great thing!
So... What Are the Key Differences?
Different types of cybersecurity and online privacy products have different functions. What are they, and what makes them unique?
Here's what experts have to say:
"You have antimalware, which is an umbrella term for antivirus protection. This should be always on, whether you're at home, at work, or traveling abroad and so on.
You have digital identity protection. This is a service that should be running at every single point in time. That's why we implement it in a web version, rather than as a security solution that runs on your device. It monitors specific locations on the Internet, the Dark Web and so on, to check if your information leaked out.
If it has, you get a notification which enables you to have a much faster response time and correct some of these issues: block your credit card, add monitoring on your social security number, and more.
Then you have your VPN, which is a privacy tool designed to protect you while you're on the go, outside of the safe environment of your home or work network, or when you’re about to do something important, like paying for an invoice, sending money to a friend, or accessing something that is blocked in a specific geographic location.
Each of these technologies addresses a very specific need, except for antimalware which should be always on and always present.
It takes a very competent technology vendor to be able to create and maintain them properly."
Bogdan Botezatu (Director of Threat Research and Reporting, Bitdefender)
Limited resources are a reality for everyone, so it is important to know how to prioritize your assets:
- The data and software on your devices (smartphone, laptop, tablet, personal computer, home assistant, smart TV)
- The information in your online accounts (email, cloud storage, social media, online banking)
- The data that results from your actions and behavior (websites you access, types of content you watch/listen to/read, online shopping habits)
All these aspects of your digital life create a unique attack surface, which is the sum of digital points that hackers can try to exploit to gain unauthorized access. That enables them to harvest more data, steal money, ask for a ransom, and even delete the hacked information entirely.
Product Overlap vs Security Bundles
Paying for products and services that have duplicate features is a legitimate concern. To make sure you are getting the most from the products and services you select, either pick one from each category, or get an all-in-one protection solution that includes everything.
There are plenty of options available to you, no matter how you choose to proceed. The important thing is to make sure you always stay protected.
tags
Author
Choose what the experts use. Award-winning cybersecurity you can trust and rely on.
View all posts
